 Windows Auditing to track user activity
Windows Auditing to track user activity
It is perhaps important to answer "who did it" without using a third party apps to point it. Windows has this feature where we need to proactively ensure that the setting are activated to produce the results.
Occasionally, someone deletes a particular important document or folder with a bunch of documents, resulting in a mission-critical data loss. Considering the described incident, few questions immediatelly arise:
§ At what date and time the incident took place?
§ Which backup should be used to restore the data?
§ Was that an accident or an intentional user action?
§ Or maybe that was some system failure that could happen again?
In Windows OSs, there is an Auditing subsystem built-in, that is capable of logging data about file and folder deletion, as well as user name and executable name that was used to perform an action. The Auditing is not enabled by default because any monitoring you use consumes some part of system resources.
Steps to enhance Auditing Objects
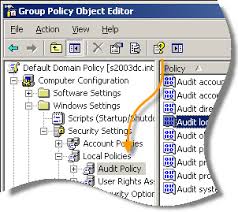
order to enable Auditing, log on to a computer that keeps shared folder structure with administrative permissions, click Start → Run and launch gpedit.msc MMC console. In a Computer Configuration node, open Windows Settings → Security Settings → Local Policies → Audit Policies folder:
Double-click Audit object access policy and select Success checkbox. Select Failure based on the org requirements. This policy enables file, folder and Windows Registry access attempts that were ended in a success.
Simply enabling policy option is not enough. It is also required to designate what folders exactly are to be watched. Usually, we require auditing shared documents and business application data folders (accounting, warehouse databases and so on) – i.e., resources accessible for editing by multiple users.
Since it's not possible to guess who has tampered with a data, we configure auditing for Everyone system group. Thus, information about any user having deleted a watched object is to be captured and stored to the event log. Open the required shared folder properties and switch to the Security tab. Click Advanced → Auditing and add Everyone to the list, then mark both Delete checkboxes:
It is highly possible that there will be too much events listed, so it is a good idea to configure the Security event log settings. To do this, click Start → Run and launch eventvwr.msc MMC console. Right-click the Security event log, select Properties and set the following options:
§ Maximum Log Size = 65536 KB (for workstations) or 262144 KB (for servers)
§ Overwrite events as needed.
Frankly, the log sizes recommended above are not calculated by any formula but are to be choosed depending on particular computer usage experience.
Finally, how do we find out the person (Windows 2003)?
When the situation comes to the question, log on to the required computer, click Start → Run and launch eventvwr.msc MMC console. Open Security event log for viewing. It is highly possible that not only the required events are logged. Right-click event log and select the View → Filter command. Consider the following events to be filtered:
§ Event Source:Security;
§ Category: Object Access;
§ Event Types: Success Audit;
§ Event ID: 560;
how do we find out the person (Windows 2008)?
When the situation comes to the question, log on to the required computer, click Start → Run and launch eventvwr.msc MMC console. Open Security event log for viewing. It is highly possible that not only the required events are logged. Right-click event log and select the Filter Current Log command. Consider the following events to be filtered:
§ Event Source: Security;
§ Category: Object Access;
§ Event Types: Success Audit;
§ Event ID: 4663;
So user activities are very likely to be noticed in event logs because it generates tens and even hundreds successful Object Access records in a second. In fact, it's easy to recover the deleted stuff from previous day backup. We were always able to answer questions "Who did it?" and "When did it happen?" either using the above activity logs or via paid apps services ManageEngine –ADAudit Plus –(give a try if you have a budget for $1.3k annually).