Tuesday, 4 October 2011
DOS Commands
Monday, 3 October 2011
Auditing SQL 2008
FROM sys.sql_logins
WHERE LOGINPROPERTY([name], 'PasswordLastSetTime') < DATEADD(dd, -60, GETDATE());
SELECT name, LOGINPROPERTY([name], 'PasswordLastSetTime') AS 'PasswordChanged'
FROM sys.sql_logins
WHERE LOGINPROPERTY([name], 'PasswordLastSetTime') < DATEADD(dd, -60, GETDATE())
AND NOT (LEFT([name], 2) = '##' AND RIGHT([name], 2) = '##');
SELECT name, LOGINPROPERTY([name], 'PasswordLastSetTime') AS 'PasswordChanged' FROM sys.sql_logins WHERE LOGINPROPERTY([name], 'PasswordLastSetTime') > DATEADD(dd, -1, GETDATE());
-- Show all logins where the password is more than 1 month
Select loginname from master..syslogins where datediff(Month,updatedate,getdate()) > 1
reference site: http://www.mssqltips.com/sql_server_dba_tips.asp
Tips to optimize SQL server performance
Top 10 Tips for Optimixing SQL Server
10. Facilitate comparisons of workload behavior with benchmarking. What are baselining and benchmarking?
9. Use performance counters to quickly get useful information about currently running operations. Operational Monitoring & Bottleneck Monitoring.8. Understand why changing server settings usually yields limited returns.
7. Identify performance bottlenecks quickly with DMVs.
6. Learn to use SQL Profiler and traces.
5. See why SANs are more than just I/O.
4. Prevent cursors and other bad T-SQL from returning to haunt applications.
3. Maximize plan reuse for better SQL Server caching.
2. Read the SQL Server buffer cache and how to minimize cache thrashing.
1. Master indexing by learning how indexes are used and how to counteract the characteristics of bad indexes.
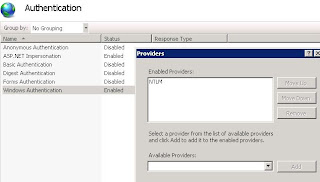
Windows authentication fail in IIS 7
Windows Authentication fails from client machines via hostname/ FQDN or ip address but works on localhost (where the application is published)
Windows authentication supports two authentication protocols, Kerberos and NTLM, which are defined in the <providers> element. When you install and enable Windows authentication on IIS 7, the default protocol is Kerberos. The <windowsAuthentication> element can also contain a useKernelMode attribute that configures whether to use the kernel mode authentication feature that is new to Windows Server 2008.
Windows authentication is best suited for an intranet environment for the following reasons:
•Client computers and Web servers are in the same domain.
•Administrators can make sure that every client browser is Internet Explorer 2.0 or later.
•HTTP proxy connections, which are not supported by NTLM, are not required.
•Kerberos version 5 requires a connection to Active Directory, which is not feasible in an Internet environment.
The following default <windowsAuthentication> element is configured at the root ApplicationHost.config file in IIS 7.0, and disables Windows authentication by default. It also defines the two Windows authentication providers for IIS 7.0.
<windowsAuthentication enabled="false">
<providers>
<add value="Negotiate" />
<add value="NTLM" />
</providers>
</windowsAuthentication>
by default for SharePoint - 80 environment only NTLM is required.
Windows authentication supports two authentication protocols, Kerberos and NTLM, which are defined in the <providers> element. When you install and enable Windows authentication on IIS 7, the default protocol is Kerberos. The <windowsAuthentication> element can also contain a useKernelMode attribute that configures whether to use the kernel mode authentication feature that is new to Windows Server 2008.
Windows authentication is best suited for an intranet environment for the following reasons:
•Client computers and Web servers are in the same domain.
•Administrators can make sure that every client browser is Internet Explorer 2.0 or later.
•HTTP proxy connections, which are not supported by NTLM, are not required.
•Kerberos version 5 requires a connection to Active Directory, which is not feasible in an Internet environment.
The following default <windowsAuthentication> element is configured at the root ApplicationHost.config file in IIS 7.0, and disables Windows authentication by default. It also defines the two Windows authentication providers for IIS 7.0.
<windowsAuthentication enabled="false">
<providers>
<add value="Negotiate" />
<add value="NTLM" />
</providers>
</windowsAuthentication>
by default for SharePoint - 80 environment only NTLM is required.

Best practice to change SharePoint service account passwords
How to change service accounts and service account passwords in SharePoint Server 2007 (MOSS2007) and in Windows SharePoint Services 3.0
microsoft site reference: http://support.microsoft.com/kb/934838
Just changing domain account password from sharepoint services and from Application Pool identity will not do.
you have to follow the above article.
in short execute the following in batch (.bat) file will also do:
----------------------------------------------------------------------------------------------------------------------------------------------------
cd %commonprogramfiles%\Microsoft Shared\Web server extensions\12\Bin
stsadm -o updatefarmcredentials -userlogin domain\enterusernamehere -password enternewpasswordhere
iisreset /noforce
stsadm -o updatefarmcredentials -userlogin domain\enterusernamehere -password enternewpasswordhere -local
iisreset /noforce
stsadm -o updateaccountpassword -userlogin domain\enterusernamehere -password enternewpasswordhere -noadmin
iisreset /noforce
stsadm -o spsearch -farmserviceaccount domain\enterusernamehere -farmservicepassword enternewpasswordhere
iisreset /noforce
stsadm.exe -o spsearch -farmcontentaccessaccount domain\enterusernamehere -farmcontentaccesspassword enternewpasswordhere
iisreset /noforce
stsadm -o editssp -title (SharedServices1 change accordingly) -ssplogin domain\enterusernamehere -ssppassword enternewpasswordhere
iisreset /noforce
----------------------------------------------------------------------------------------------------------------------------------------------------
Just changing domain account password from sharepoint services and from Application Pool identity will not do.
you have to follow the above article.
in short execute the following in batch (.bat) file will also do:
----------------------------------------------------------------------------------------------------------------------------------------------------
cd %commonprogramfiles%\Microsoft Shared\Web server extensions\12\Bin
stsadm -o updatefarmcredentials -userlogin domain\enterusernamehere -password enternewpasswordhere
iisreset /noforce
stsadm -o updatefarmcredentials -userlogin domain\enterusernamehere -password enternewpasswordhere -local
iisreset /noforce
stsadm -o updateaccountpassword -userlogin domain\enterusernamehere -password enternewpasswordhere -noadmin
iisreset /noforce
stsadm -o spsearch -farmserviceaccount domain\enterusernamehere -farmservicepassword enternewpasswordhere
iisreset /noforce
stsadm.exe -o spsearch -farmcontentaccessaccount domain\enterusernamehere -farmcontentaccesspassword enternewpasswordhere
iisreset /noforce
stsadm -o editssp -title (SharedServices1 change accordingly) -ssplogin domain\enterusernamehere -ssppassword enternewpasswordhere
iisreset /noforce
----------------------------------------------------------------------------------------------------------------------------------------------------
InfoPath published Forms error using DNS Record: Event ID 5566, in MOSS 2007 64Bit
InfoPath Form Services Error accessing data source eventid 5566 in SharePoint 2007
SYMPTOM:
Forms when accessed through the browser using DNS Record (A Record created in DNS: intranet) was showing error. There are no issues when accessing the same forms using hostname(http://intra-app1)
ENVIRONMENT:
SharePoint 2007 SP2 (CU August 2011: 12.0.0.6565), OS: Windows 2008 R2 Enterprise Edn.
SCOPE:
Published Forms opens properly from client access using WFE server hostname (http://intra-app1 ) (Hostname of WFE: intra-app1)
However, the forms could not be accessed using the DNS entry (http://intranet). shoots errors ID 5566 as seen below:
ACTION:
Inorder to solve this we configured the following setting in the registry for disabling the loopback check in the registry using the following method.
In Registry Editor, locate and then click the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
Right-click Lsa, point to New, and then click DWORD Value.
Type DisableLoopbackCheck, and then press ENTER.
Right-click DisableLoopbackCheck, and then click Modify.
In the Value data box, type 1, (hexadecimal) and then click OK.
No need to either restart the server or carryout IISreset /noforce
This is enough, just try accessing portal using the DNS and the published forms using DNS record (http://intranet). This should solve the problem.
Also, make sure AAM (Alternet Access Maping: http://intranet) to Intranet Zone is configured at the CA level .
Subscribe to:
Comments (Atom)



